MANTA—The Brain of Tomorrow’s Metaverse (2/4)
How to guarantee data security?
Today, data is becoming an essential factor for all forms of production, and the value of data will only be more pronounced in the Metaverse.
Even though today, the Metaverse is restricted to photos, graphical effects and games, in the future, the Metaverse will integrate the real and the virtual worlds and affect every aspect of our lives. To provide people with a more immersive experience, the Metaverse must first become a gigantic data hub and computing power accelerator.
User data include but are not limited to information about their identity, biometrics, behavioural patterns, social relationship, assets, etc. Even the relationship status and brain wave patterns of users may become useful to collect. The constant updating and production of user private data will be essential for the Metaverse as a fundamental resource as well as a means of production.
For this reason, to protect private data from being illegally collected, stored, managed and used, we must develop tech solutions and regulations to control how data are used. Therefore, privacy-preserving computation will be essential for the Metaverse.
What is privacy-preserving computation?
Privacy Computing: Concept, Connotation and Its Research Trend published in 2016 defined privacy-preserving computation as “a series of theories and methodology governing the full-life-cycle protection of private data, as well as a computable model and axiomatic system facilitating the separation of the right to own, to manage and to use private data, the compensation for data leakage and the assessment of the complexity thereof”.

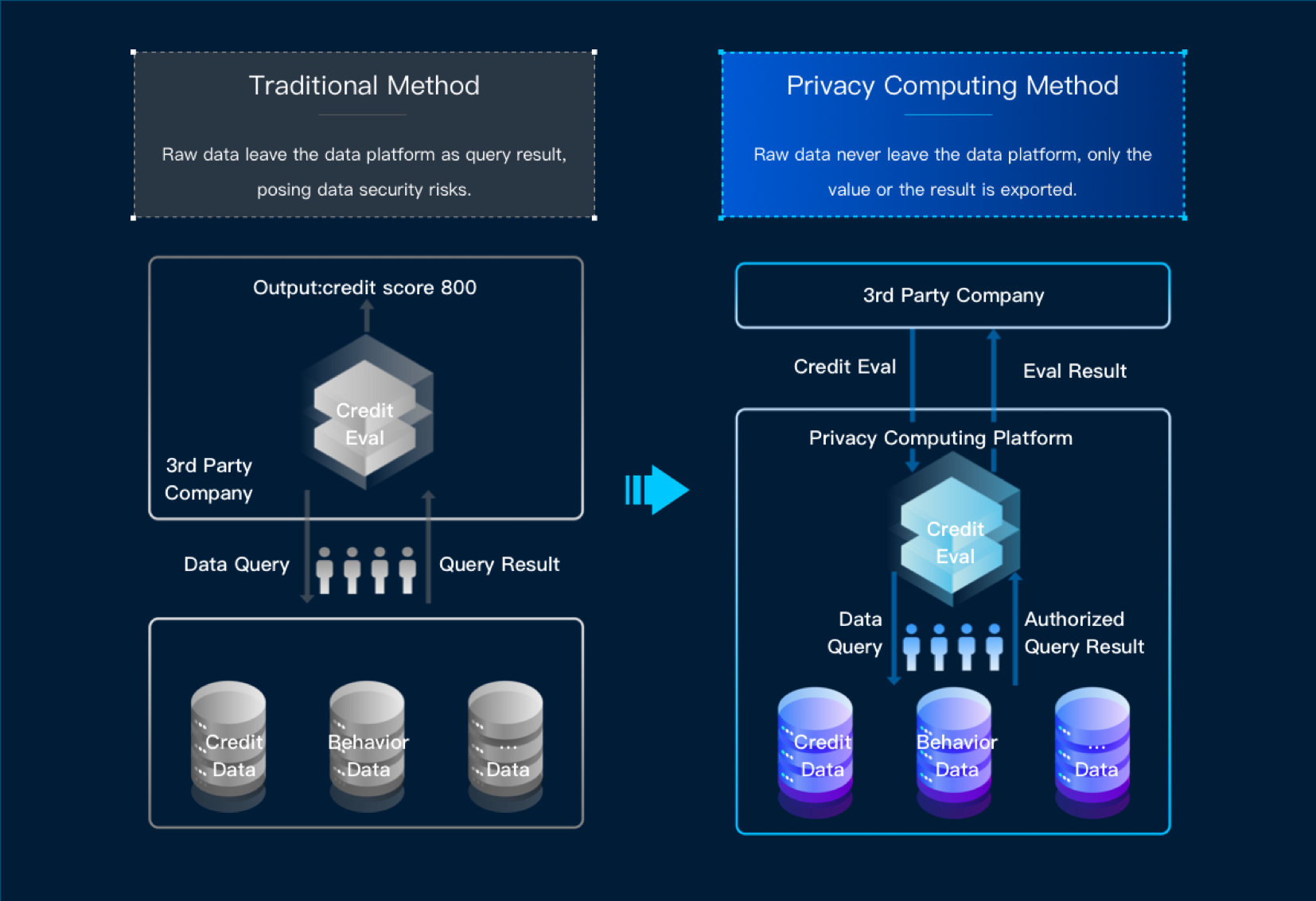
Privacy-preserving computation is not a standalone technology but rather a system of technologies including cryptology, AI, security hardware, etc. Its purpose is to guarantee the full-life-cycle security of data so that data can be computed and analyzed in a non-transparent way. This way, we can effectively extract value from data, and data can be bought and sold as a resource in the market.
Of these technologies, secure multi-party computation is a branch under cryptology dealing with the protection of data security when a group of non-trusting parties collaborate in a computing task. It guarantees that no single party can know the computing results other than those of the part it is assigned.
While a trusted execution environment (TEE) based on trusted hardware facilitates private data processing and computing as well as the operation of trusted apps. This guarantees that, during execution, data is safe and non-transparent.
In addition, federated learning based on AI is a distributed learning technology integrating cryptology and AI. It aims to protect information and data security during the exchange of big data. This technology is useful for helping industries build machine learning models. Whatever the specific privacy-preserving computation technology, its goal is to make data usable and computable without making them transparent and recognizable.
When it comes to application, projects and businesses are constantly trying to integrate blockchain technologies and privacy-preserving computation. On the one hand, data on blockchain need to be protected by privacy-preserving algorithms. On the other, blockchain can serve as a foundation or hub for collaborative privacy-preserving computation tasks.
Thanks to technological advances, blockchain is transitioning from an immutable, traceable and transparent distributed bookkeeping technology into a distributed network data management technology, which utilizes cryptology and distributed consensus protocols for secure data transmission and access so that data can be cross-verified and is globally consistent and immutable.
Although privacy-preserving computation can guarantee the privacy of input data during multi-party collaborative computing tasks, the original data, the computing process, as well as the results, still need to be verified. Thanks to blockchain features such as distributed bookkeeping, smart contract, consensus mechanism, etc, the original data stored on-chain can be authenticated, and the key data and essential steps of computing tasks can be traced back so that the entire process is verifiable.
The full potential of blockchain can only be actualized in combination with practical scenarios and other technologies. Smooth data circulation, the extraction of value from data as well as privacy-preserving computation are perfect areas for blockchain technologies to shine.
Conversely, by applying blockchain’s trusted computing to privacy-computing computation, we can make its process verifiable. The two technologies will add to each other and make for better synergy in data usage on a broader level.
Privacy-preserving computation has already become a practical demand in VR and AR, and it will only be more crucial when building the Metaverse. Through encrypted sharing of private data, privacy-preserving computation offers a solution to ending data abuse on the traditional internet. This way, an endless variety of data can be converted into the fuel for the development of the Metaverse.

MANTA—The Brain of Tomorrow’s Metaverse (1/4)
MANTA—The Brain of Tomorrow’s Metaverse (3/4)
MANTA—The Brain of Tomorrow’s Metaverse (4/4)
Twitter: https://twitter.com/MatrixAINetwork/status/1527552546188951552?s=20
Medium: https://matrixainetwork.medium.com/manta-the-brain-of-tomorrows-metaverse-2-4-19074ab425e5